Symantec Solutions
Endpoint Management Suites
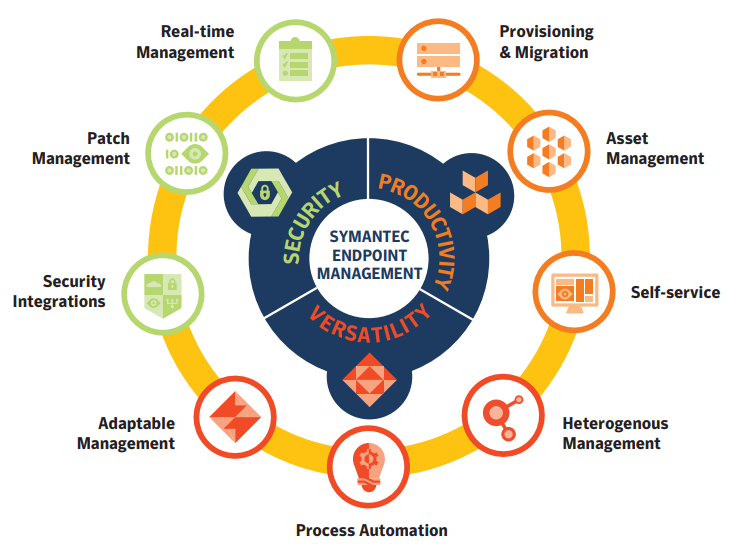
Keeping users productive and protected as you manage an increasingly complex IT environment – with a wider range of devices and operating systems, more mobile and remote users, and more vulnerabilities and threats to combat – requires greater versatility than ever before.
Symantec endpoint management solutions strengthen endpoint security through real-time management, powerful patch management, and integrations with other Symantec security solutions. They maximize user productivity by speeding and simplifying software and operating system (OS) deployment and migration, integrating asset management, and enabling end-user self-service. And their versatility enables you to extend these key capabilities across all major desktop and server operating systems, securely manage endpoints inside and outside the perimeter, and automate common IT processes to reduce costs.
Symantec Ghost™ Solution Suite is an industry leading and award winning solution for deploying and managing desktops, laptops, tablets, and servers. From a single management console, you can quickly and easily migrate to the latest operating systems, inventory machines, deploy software, and perform custom configurations across multiple hardware platforms and OS types including Windows, Mac, and Linux.
Ghost Solution Suite 3.3 has a new web-based console designed specifically for technicians with minimal experience. It complements the full console and is simple to use with built-in wizards for common tasks such as Windows 10 migration and deploying images. It has a modern UI and works with any browser. With the web console, frequently run jobs can be delegated to frontline technicians to optimize resources and reduce costs. The web console is also highly scalable, so a large number of technicians can use it simultaneously.
Endpoint Management Modular Suites
Symantec Client Management Suite (CMS) helps manage, patch, and remediate application and OS configurations for desktops, laptops and servers throughout their lifecycle to strengthen endpoint security and maximize user productivity. CMS supports all major operating systems, provides both real-time and persistent management of endpoints inside and outside the perimeter, and has extensive deployment and patch management capabilities.
Client Management Suite 8.5 introduces several new compelling features and enhancements including:
- Time Critical Management
- Endpoint Compliance and Quarantine
- Automated Vulnerability-based Scanning and Remediation
- Modern UI Workspaces
- Updated Self-service Software Portal
Symantec Server Management Suite provides IT administrators with a comprehensive solution for managing physical and virtual servers across a broad array of platforms. The suite provides solutions to provision, control, automate, and monitor servers from a central console. With these tools, organizations gain and maintain control of their servers, reduce service interruptions, and increase uptime.
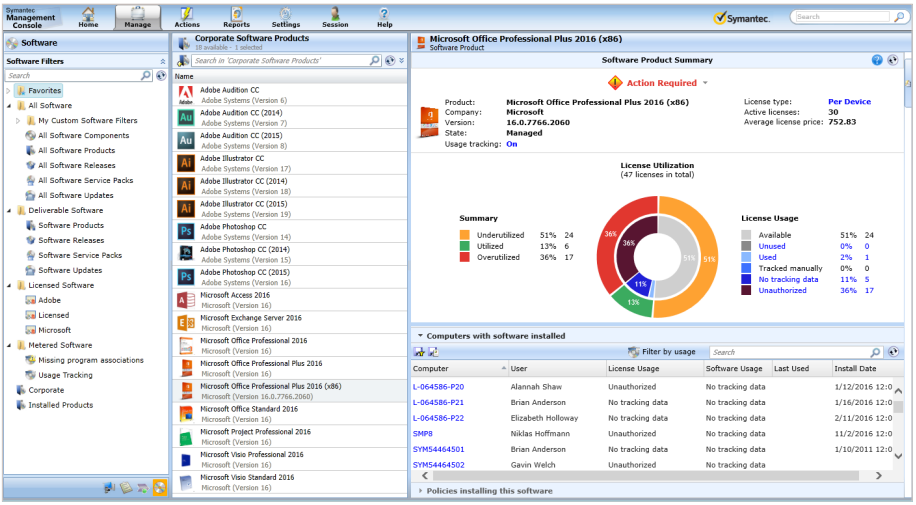
Symantec Asset Management Suite enables organizations to take control, uncover savings, and ensure compliance of IT assets. With an accurate picture of assets throughout their lifecycle, IT can optimize investments, eliminate the purchase of unnecessary software, and avoid penalties and fines due to non-compliance.
Service Management
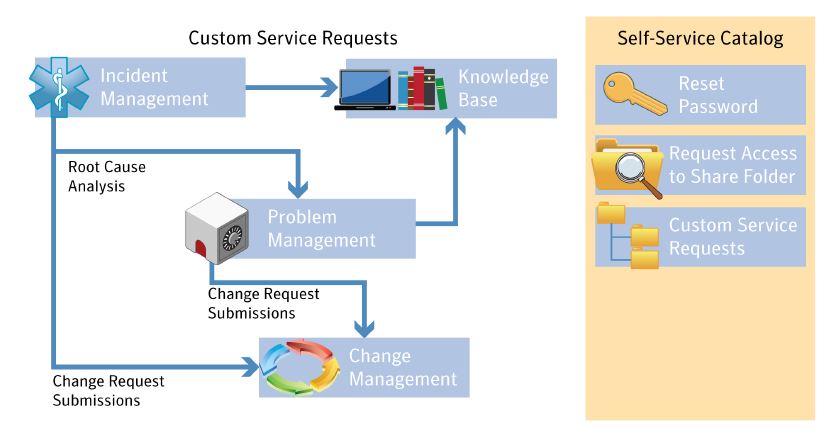
Symantec ServiceDesk offers ITIL-based helpdesk functionality for quick incident, change, and problem management. ServiceDesk also includes a knowledge management system, full reporting, and wraps these in an easy to use and configurable service catalog.
ServiceDesk also integrates directly with other Symantec endpoint management solutions including IT Management Suite, Client Management Suite, Asset Management Suite, and Server Management Suite. ServiceDesk helps reduce service interruptions, accelerate service restorations, correct systemic issues, and reduce overall downtime—allowing optimization of valuable IT resources and expenses.
Based on best practices, ServiceDesk is designed for:
- Fast implementation
- Upgradeable, rules-based configuration
- Direct integration with Symantec endpoint management solutions
- Optimization of IT processes
Information and Identity Protection
BeyondTrust Privileged Remote Access provides visibility and control over third-party vendor access, as well as internal remote access, enabling organizations to extend access to important assets, but without compromising security.
Privileged Remote Access Features & Capabilities:
- Privileged Access Control: Enforce least privilege by giving users the right level of access.
- Monitor Sessions: Control and monitor sessions using standard protocols for RDP, VNC, HTTP/S, and SSH connections.
- Reduce the Attack Surface: Reduce attacks by consolidating the tracking, approval, and auditing of privileged accounts in one place and by creating a single access pathway.
- Integrate with Password Management: Inject credentials directly into servers and systems with just one click, so users never need to know or see plain text credentials.
- Mobile & Web Consoles: Use mobile apps or web-based consoles anytime, anywhere.
- Audit & Compliance: Create audit trails, session forensics, and other reporting features by capturing detailed session data in real-time or post- session review, and provide attestation reports to prove compliance.
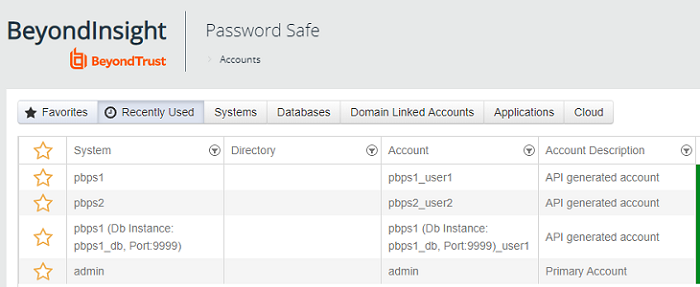
BeyondTrust Password Safe unifies privileged password and privileged session management, providing secure discovery, management, auditing, and monitoring for any privileged credential. Password Safe enables organizations to achieve complete control and accountability over privileged accounts.
Password Safe Features and Capabilities:
- Continuous Automated Account Discovery and Auto-Onboarding: Leverage a distributed network discovery engine to scan, identify, and profile all assets. Dynamic categorization allows autoonboarding into Smart Groups for efficient management.
- Secure SSH Key Management: Automatically rotate SSH keys according to a defined schedule and enforce granular access control and workflow. Leverage private keys to securely log users onto Unix/Linux systems through the proxy, with no user exposure to the key, and with full privileged session recording.
- Application-to-Application Password Management: Eliminate hard-coded or embedded application credentials through an adaptable API interface that includes an unlimited number of Password Caches for scalability and redundancy.
- Enhanced Privileged Session Management: Live session management enables true dual control, enabling admins to record, lock, and document suspicious behavior without killing sessions – or productivity.
- Adaptive Access Control: Evaluate just-in-time context and simplify access requests by considering the day, date, time, and location when a user accesses resources to determine their authorization to access those systems.
- Advanced Privileged Threat Analytics: Measure asset characteristics and user behaviors from one day to the next, assessing the scope and speed of any changes to alert you to suspicious deviations.
BeyondTrust Privilege Management for Desktops elevates privileges to known good applications that require them, controls application usage, and logs and reports on privileged activities using security tools already in place.
Features and Capabilities:
- Least Privilege Enforcement: Elevate privileges to applications for standard users on Windows or MacOS through fine-grained policy-based controls, providing just enough access to complete a task.
- Seamless Application Control: Deliver trust-based application whitelisting with a flexible policy engine to set broad rules. Tailored options enable organizations to choose automatic approval for advanced users – protected by full audit trails – or utilize challenge-response codes. Application whitelisting rules can be applied based on software origin as well.
- Complete Auditing and Reporting: Provide a single, unimpeachable audit trail of all user activity that speeds forensics and simplifies compliance.
- Privileged Threat Analytics: Correlate user behavior against asset vulnerability data and security intelligence from best-of-breed security solutions to provide an overall picture of end-user risk. Integrations with the Security Ecosystem: Built-in connectors to a host of third-party solutions, including help desk applications, vulnerability management scanners, and SIEM tools, ensure that organizations realize a return on their security investments.
- Integrations with the Security Ecosystem: Built-in connectors to a host of third-party solutions, including help desk applications, vulnerability management scanners, and SIEM tools, ensure that organizations realize a return on their security investments.
Endpoint Security

Unmatched Endpoint Safety for Your Organization!
Symantec Endpoint Security delivers the most complete, integrated endpoint security platform on the planet. As an on-premises, hybrid, or cloud-based solution, the single-agent Symantec platform protects all your traditional and mobile endpoint devices, and uses artificial intelligence (AI) to optimize security decisions. A unified cloud-based management system simplifies protecting, detecting and responding to all the advanced threats targeting your endpoints.
- Keep your business running. Compromised endpoints are highly disruptive to business. Innovative attack prevention and attack surface reduction delivers the strongest security across the entire attack life cycle (e.g., stealthy malware, credential theft, fileless, and “living off the land” attacks).
- Prevent the worst-case scenario. Full blown breaches are CISOs’ worst nightmare. Deliver detection and remediation of persistent threats with sophisticated attack analytics and prevention of AD credential theft.
- Manage smarter. Work less. Intelligent automation and AI-guided policy management enhance administrator productivity; Symantec experts fortify SOC teams to meet customer needs without hiring additional headcount.
- Manage everything in one place. Integrated Cyber Defense Manager (ICDm) is a single cloud management console that strengthens overall endpoint security posture.
- Endpoint security delivered your way. With a single agent, protection across traditional and mobile devices, and on-prem, cloud or hybrid management.

Your staff relies on mobility and anywhere-access to stay productive. Unfortunately, your sensitive data may be unknowingly synchronized from the cloud, and at risk when devices are lost or stolen.
Symantec Endpoint Encryption protects sensitive information and ensures regulatory compliance. It encrypts all files on the hard drive, sector-by-sector, for maximum security. It supports Windows, Mac, tablets, self-encrypting drives, and removable media (USB drives, external hard drives, and DVDs). For maximum flexibility, Symantec Endpoint Encryption also manages BitLocker and File Vault-protected devices.
- Launch and manage encryption from a single console
- Facilitate user access with single sign-on support
- Minimize risks associated with devices and removable media
- Supports Symantec, BitLocker and File Vault encryption
Process Automation
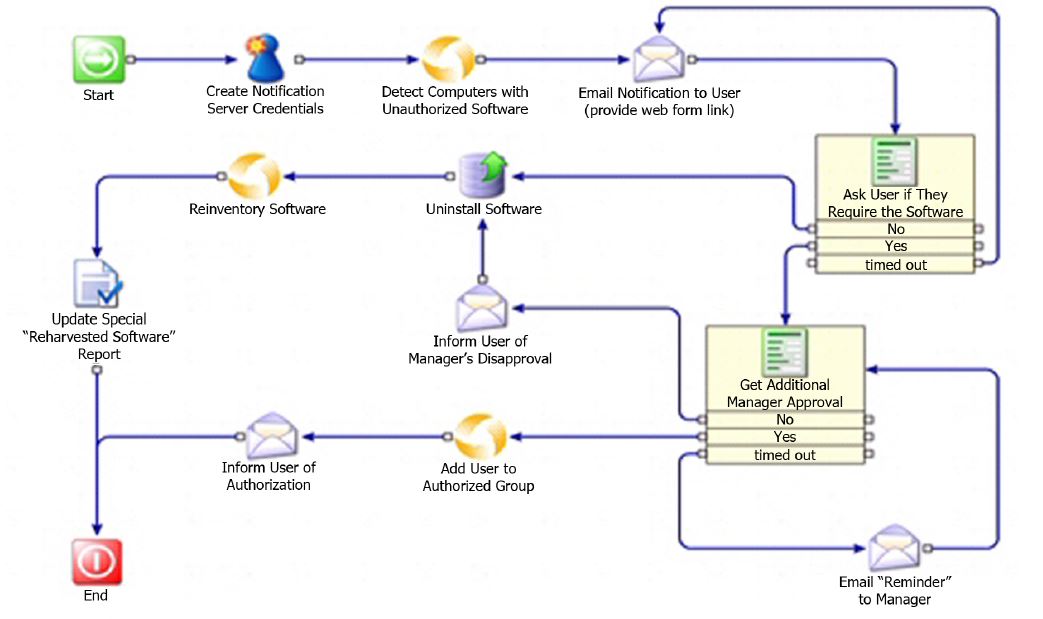
Symantec Workflow is a graphical .NET application and security process development framework.
You can use Workflow to build business and security processes, which are definable, repeatable, controllable, auditable, and reduce overall workload. The Workflow framework also lets you create Workflow processes that integrate Symantec tools into your organization’s unique business processes.

